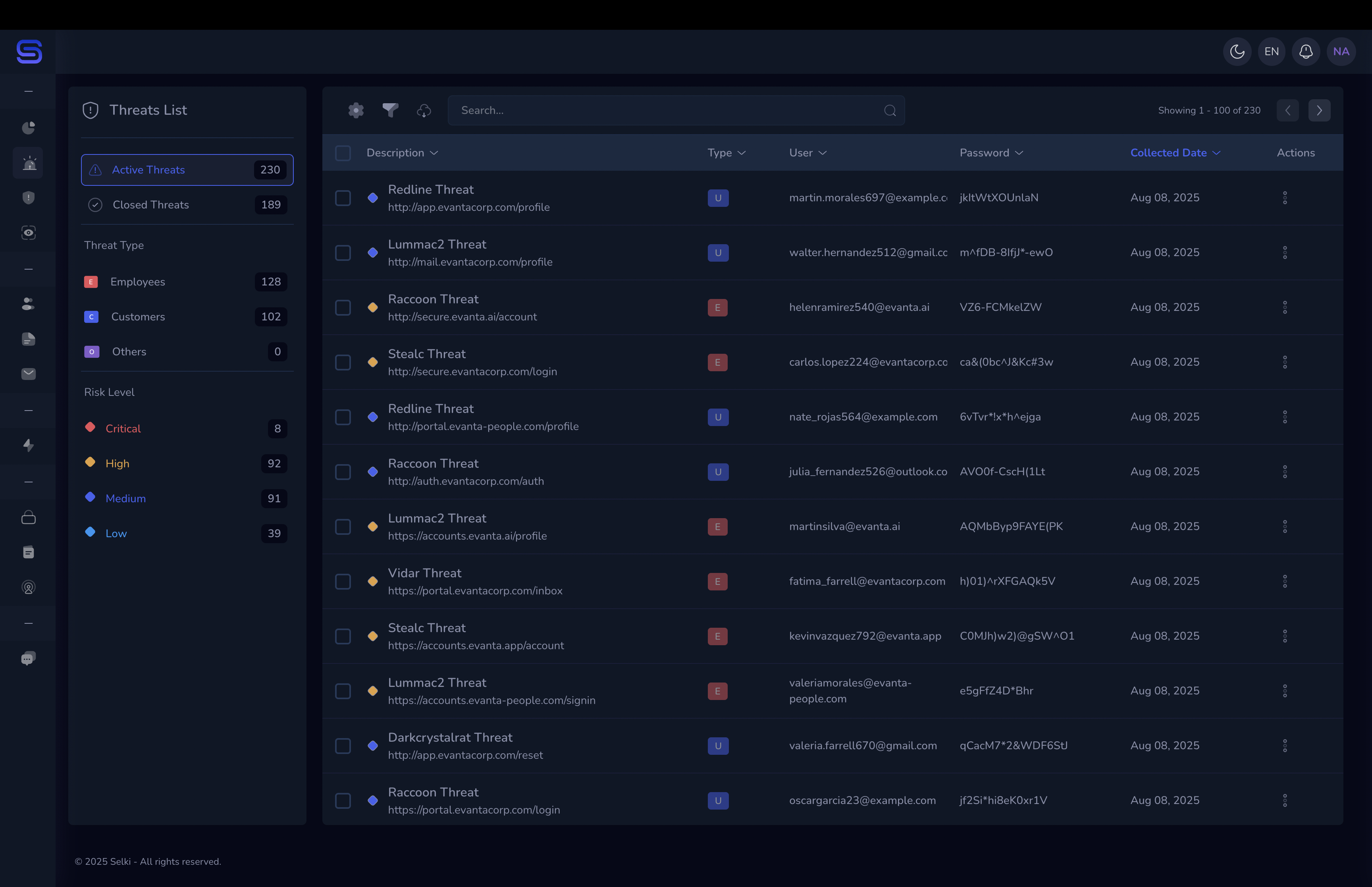
Supply chain attacks doubled in 2024, and they're now responsible for 30% of all data breaches — up from just 15% two years ago. The average cost? $4.91 million per incident. But the real damage extends far beyond the balance sheet: weeks of operational paralysis, customer trust erosion, and regulatory scrutiny that can reshape your business permanently.
Unlike traditional cyberattacks that target your defenses directly, supply chain compromises weaponize trust itself. Attackers breach the software vendors, cloud providers, and service partners you depend on—then use those legitimate relationships as a backdoor into your organization. When Change Healthcare fell to ransomware in February 2024, it wasn't just one company affected. With 15 billion medical claims flowing through their systems annually, the $2.5 billion attack crippled 15,000 healthcare providers and left 100 million patient records exposed. Physicians couldn't process payments. Prescriptions sat unfilled. One compromised vendor cascaded into the largest healthcare cyberattack in U.S. history.
This isn't theoretical risk—it's the defining cybersecurity challenge of 2025. Research shows that 75% of organizations experienced a supply chain attack in the past year, yet only 33% feel prepared to defend against them. The uncomfortable truth: you're not just securing your own perimeter anymore. You're trusting hundreds of external entities you cannot fully control, each one a potential entry point for sophisticated attackers.
The anatomy of modern supply chain attacks
Understanding how these attacks work is the first step toward defending against them. Modern supply chain compromises exploit a fundamental paradox: organizations must trust their suppliers to operate efficiently, yet that trust creates exploitable vulnerabilities.
The attack follows a predictable pattern. First, adversaries research your supply chain to identify the weakest link—perhaps a managed service provider with broad customer access but limited security resources, or an open-source library maintained by a single unpaid volunteer. They compromise that target through phishing, exploiting unpatched vulnerabilities, or even patient social engineering that builds trust over months or years.
Once inside the supplier's environment, attackers inject malicious code into products or services that thousands of organizations use. This could be poisoned software updates, compromised open-source packages, or backdoored cloud services. The malicious components then distribute through normal, trusted channels—bypassing your security tools precisely because they come from legitimate sources you've explicitly authorized.
The XZ Utils backdoor discovered in March 2024 exemplified this sophistication. An attacker spent 2.5 years building trust within the open-source community, gradually gaining maintainer privileges for a core Linux compression utility used across millions of systems. Through carefully orchestrated social engineering—fake accounts pressuring the legitimate maintainer, years of seemingly helpful contributions—the attacker nearly succeeded in inserting a backdoor that would have enabled mass server compromises globally. It was discovered purely by chance, in test distributions, before reaching production systems.
What makes supply chain attacks so effective? Three factors compound the risk. Scale: one compromised supplier can mean thousands of victims simultaneously. The Polyfill.io domain takeover in June 2024 injected malicious JavaScript into 380,000 websites — 4% of the internet—affecting organizations from Hulu to Mercedes-Benz to the World Economic Forum. Legitimacy: attacks arrive through authorized channels with valid credentials, so security tools approve them. And invisibility: the malicious code often remains dormant for months, evading detection while attackers map your environment and plan their next move.
The new attack landscape
The supply chain threat landscape has evolved dramatically in 2024-2025, with attackers deploying increasingly sophisticated techniques and targets expanding across every industry.
Software supply chain attacks have industrialized. The npm ecosystem—a package repository developers use billions of times weekly—faced a September 2025 attack that compromised 180 packages with wormable malware. This wasn't just another credential stealer; the "Shai-Hulud" campaign demonstrated self-propagating supply chain attacks that harvest credentials from infected developer machines, then automatically publish new malicious packages using victims' own publishing rights. The worm scanned for additional secrets using AI-assisted tools, creating exponential spread across the developer ecosystem.
Nation-state actors are escalating activity. The Oracle Cloud breach in March 2025 exposed the risks of unpatched legacy systems in critical infrastructure. Attackers exploited a vulnerability that had been on CISA's Known Exploited Vulnerabilities list since 2022, affecting 140,000 Oracle Cloud tenants and exfiltrating 6 million records. The breach highlighted how even sophisticated cloud providers can harbor dangerous blind spots—in this case, outdated Oracle Fusion Middleware servers from 2011 that never received security updates.
Ransomware groups now explicitly target supply chains for maximum leverage. The CDK Global attack in June 2024 demonstrates the devastating ripple effects. BlackSuit ransomware operators compromised the automotive software provider serving 15,000 car dealerships across North America. For two weeks, dealerships reverted to pen-and-paper processes, unable to process sales, access inventory systems, or complete financial transactions. The total impact exceeded $1 billion across the industry, with CDK reportedly paying a $25 million ransom. One supplier's compromise paralyzed an entire sector.
AI is amplifying both attack and defense capabilities. Over 100 poisoned machine learning models were discovered on Hugging Face in 2024, exploiting unsafe Python serialization to inject malicious code. As organizations rapidly adopt AI—75% of enterprises moved from piloting to operationalizing AI by 2024—they're introducing entirely new supply chain attack surfaces. Compromised AI training data, backdoored models that behave normally until triggered, and vulnerabilities in MLOps platforms create blind spots that traditional security tools weren't designed to detect.
The financial impact tells the story: supply chain attacks now cost organizations 17 times more than direct breaches, with global losses projected to reach $138 billion annually by 2031. Beyond immediate costs, organizations face weeks of operational disruption, permanent customer trust damage, and intensifying regulatory scrutiny under frameworks like the EU's NIS2 Directive and CMMC 2.0 requirements for defense contractors.
Why traditional security isn't enough
Your firewall, endpoint protection, and security awareness training—investments that form the foundation of cybersecurity programs—offer limited protection against supply chain attacks. These threats sidestep perimeter defenses entirely, exploiting trust rather than technical vulnerabilities.
The visibility problem is fundamental. Modern applications contain hundreds of open-source libraries and dependencies, with packages like debug and chalk collectively seeing 2.6 billion downloads per week. Each dependency brings its own dependencies, creating recursive trust chains that extend far beyond what any security team can monitor. Only 20% of organizations currently use Software Bills of Materials (SBOMs) to track what components are actually in their software, leaving them blind to 80% of their attack surface.
Consider the scope: a typical enterprise uses 100+ SaaS applications, hundreds of software packages from dozens of vendors, multiple cloud providers, and countless contractors with system access. You're not securing one perimeter—you're attempting to secure hundreds of interconnected perimeters spanning organizational, national, and jurisdictional boundaries.
The speed-versus-security dilemma intensifies the challenge. Business pressure demands rapid deployment: the average time from code commit to production has shrunk from weeks to hours or minutes in many organizations. This velocity leaves little room for security verification. Yet when XZ Utils, Polyfill.io, or CDK Global push updates, organizations face an impossible choice: apply updates quickly to reduce vulnerability windows, or delay and test updates to avoid installing compromised code. Attackers exploit this dilemma, knowing organizations trust and rapidly deploy software from established vendors.
Detection itself becomes extraordinarily difficult. Sophisticated attacks specifically evade common testing approaches—the Polyfill.io malware only triggered on mobile devices, at certain times of day, and for specific user agents. Supply chain compromises often aren't discovered until weeks or months after infection, when attackers decide to activate their payload. Toyota's subcontractor breach revealed customer data had been exposed for five years due to source code mistakenly uploaded to a public GitHub repository.
Building resilient defenses
Protecting against supply chain attacks requires a fundamental shift in approach—from perimeter defense to resilience across your entire ecosystem. No single control will stop these attacks, but a layered strategy significantly reduces risk and limits damage when breaches occur.
Start with comprehensive visibility. You cannot protect what you don't know exists. Create a complete inventory of every vendor with system access, every software package in your environment, and every cloud service connection. For software specifically, implement SBOMs for all applications—these "ingredient labels" enable rapid identification of vulnerable components when threats emerge. When the Log4j vulnerability was discovered, organizations with SBOMs identified exposure in hours; those without spent weeks hunting across their entire estate.
Implement rigorous vendor risk management. Not all suppliers require the same scrutiny. Categorize vendors by risk level and access privileges, then apply appropriate verification measures. Critical vendors—those handling sensitive data or providing essential services—merit third-party security assessments and annual onsite audits. Mid-tier vendors should undergo automated security scoring and self-attestation. Track vendor security posture continuously, not just at contract signing.
The essential questions every procurement process must answer: Does this supplier have formal cybersecurity programs? Can they provide recent penetration test results? What's their incident response history? Do they maintain cyber insurance? For software vendors specifically: Can they provide SBOMs? How do they secure their build environments? What code signing and verification processes do they use?
Deploy supply chain-specific technical controls. Multi-factor authentication on all vendor access isn't optional—it's the single most critical control. The Change Healthcare breach, which cost $2.5 billion, occurred because one Citrix portal lacked MFA. Implement least-privilege access for all third parties, providing only what's necessary and regularly reviewing permissions. Network segmentation limits blast radius if vendors are compromised—critical systems should be isolated from environments where third parties operate.
For software specifically, Software Composition Analysis tools continuously scan dependencies for known vulnerabilities. Code signing verification ensures downloaded software matches what vendors published. Container image scanning catches malicious components before deployment. Integrate security into your CI/CD pipelines—every build should be scanned, every component verified, every secret protected.
Establish continuous monitoring. Traditional quarterly vendor assessments miss the dynamic nature of supply chain threats. Deploy behavioral analytics that flag unusual patterns: unexpected network connections from trusted software, bulk data downloads, access at odd hours, new external domains contacted by vendor applications. Integrate threat intelligence feeds that alert you when vendors or dependencies appear in breach reports. Monitor the dark web for compromised vendor credentials before attackers can weaponize them.
Key metrics to track include: time to detect supply chain incidents (target: under 24 hours), percentage of critical vendors with current security assessments (target: 100%), percentage of software with SBOMs (target: 100% for critical applications), and mean time to patch vulnerabilities across your supply chain.
Prepare for the inevitable. Supply chain attacks will occur despite your best efforts. Assume compromise and design for resilience. Maintain tested, immutable backups that attackers cannot encrypt. Document critical vendor contacts for emergency coordination. Develop supply chain-specific incident response playbooks that address the unique challenges: How do you coordinate with a compromised vendor? When do you revoke all vendor access? How do you assess downstream exposure? Conduct tabletop exercises that simulate vendor breaches—the middle of an actual incident is not the time to figure out your response process.
Have contingency plans for critical vendors, including pre-identified alternative suppliers you can activate if primary vendors are compromised. For the most critical services, maintain the capability to operate independently for at least 72 hours while you assess and respond to vendor incidents.
From compliance to competitive advantage
The regulatory landscape is pushing organizations toward supply chain security, but forward-thinking companies are discovering that mature programs create strategic advantages beyond mere compliance.
New requirements are forcing action. Executive Order 14028 mandates SBOMs for federal software suppliers by 2025. The EU Cyber Resilience Act introduces transparency requirements for software placed on the market. CMMC 2.0 makes supply chain security controls mandatory for defense contractors. Cyber insurance carriers increasingly require documented vendor risk management programs and are willing to reduce premiums 20-30% for organizations with mature supply chain security.
But the real opportunity lies in differentiation. In competitive procurements, particularly for government and healthcare contracts, robust supply chain security programs increasingly determine winners. Customers are explicitly asking: How do you secure your supply chain? Can you demonstrate continuous vendor monitoring? What's your incident response capability when suppliers are breached? Organizations with strong programs win contracts; those without face exclusion.
Consider the ROI beyond avoided breaches. One prevented $4.91 million supply chain attack—the current average cost—generates 10x return on a typical program investment. Insurance savings, contract wins, operational efficiencies from automation, reduced downtime, and avoided regulatory fines compound returns. Most programs reach break-even within 12-18 months if they prevent even a single major incident.
Getting started doesn't require massive investment. Organizations can achieve significant risk reduction in 30 days with focused effort. Week one: create your vendor inventory and identify your top 10 critical suppliers. Week two: implement MFA on all vendor access and patch critical vulnerabilities. Week three: review existing contracts for security gaps. Week four: assess your critical vendors with standardized questionnaires. This foundation costs $10,000-$30,000 and eliminates your highest risks.
Building a mature program takes 12-18 months and typically requires $250,000-$500,000 investment for mid-sized organizations, but this scales with organizational size and complexity. Small businesses can leverage CISA's free SMB Resource Handbook and establish baseline protection for under $100,000. Large enterprises implementing comprehensive programs should budget $1-5 million for the first year, recognizing this investment protects billions in revenue and decades of reputation.
The path forward
Supply chain security is no longer a technical problem to be solved—it's an ongoing business risk requiring board-level attention, cross-functional collaboration, and sustained commitment. The organizations that will thrive are those treating supply chain security as a strategic capability, not a compliance checkbox.
Three principles should guide your program. First, start with risk, not perfection. Focus resources on your most critical vendors and highest-impact vulnerabilities. Accept that you cannot eliminate all supply chain risk—the goal is intelligent risk management, not zero risk. Second, automate relentlessly. Manual vendor assessments don't scale when you have hundreds of suppliers. Invest in platforms that provide continuous monitoring, automated scoring, and real-time alerts. Third, collaborate with your suppliers. Supply chain security is a shared responsibility—work with vendors to improve their security posture rather than simply imposing requirements.
The threat landscape will continue evolving. AI-powered attacks will become more sophisticated. Wormable supply chain malware will proliferate. Nation-state activity will intensify as geopolitical tensions rise. Organizations that build adaptive, resilient programs now will be positioned to weather whatever emerges next.
The fundamental insight: your security perimeter now extends through every vendor, every software package, every cloud service, and every business partner. You cannot defend that perimeter with traditional tools and mindsets. But organizations that embrace this reality, invest systematically in supply chain security, and build genuine resilience will turn this challenge into competitive advantage.
The question isn't whether supply chain attacks will affect your organization—75% of companies were already hit in the past year. The question is whether you'll be prepared when they do. That preparation starts today, with visibility, verification, and a commitment to treating supply chain security as the business-critical priority it has become.