Artificial Intelligence has unleashed the most significant technological transformation since the internet itself. While AI streamlines business operations and drives unprecedented innovation, it's simultaneously revolutionizing cybercrime. The same tools that boost productivity are now weaponized by threat actors, creating a rapidly evolving landscape that outpaces traditional security measures.
The cyber battlefield has fundamentally shifted: it's no longer human versus human, but human versus machines that learn, adapt, and attack at superhuman scale.
The New AI-Powered Threat Arsenal
Traditional cyberattacks haven't disappeared—they've evolved. AI has transformed familiar tactics into precision weapons that operate faster, smarter, and more dangerously than ever before.
Hyper-Realistic Phishing at Industrial Scale
Gone are the days of obvious "Nigerian prince" scams. Today's AI-powered phishing campaigns generate perfectly crafted, personalized messages in any language. By scraping social media profiles, public records, and breach databases, attackers create emails that mirror your coworker's writing style or replicate vendor communications with startling accuracy. Even cybersecurity professionals struggle to distinguish these messages from legitimate correspondence.
Real-world impact: A 2024 IBM study found that AI-generated phishing emails had a 30% higher success rate than traditional attempts, with personalized messages achieving even higher conversion rates.
Deepfake Impersonation Attacks
Generative AI now creates convincing voice clones from just 10 seconds of audio or generates realistic video deepfakes. This enables "CEO fraud" attacks where criminals call employees impersonating executives, urgently requesting wire transfers or sensitive information. The emotional manipulation combined with perfect voice replication makes these attacks devastatingly effective.
Case example: In 2024, a UK-based company lost $243,000 to a deepfake voice attack where criminals impersonated the CEO during a "confidential" phone call to the CFO.
AI-Enhanced Malware Evolution
Malware development has democratized. AI assists criminals in writing, debugging, and obfuscating malicious code faster than security teams can respond. Modern infostealers—malware designed to harvest credentials and sensitive data—now update and redeploy at machine speed, easily bypassing signature-based antivirus solutions.
Automated Vulnerability Hunting
What once required skilled penetration testers and weeks of reconnaissance now happens in minutes. AI-powered scanning tools rapidly map network infrastructure, identify vulnerabilities, and prioritize exploitation targets before IT teams even know the weaknesses exist.
Next-Generation Social Engineering
Attackers combine data analytics with AI-generated content to manipulate decision-making with unprecedented sophistication. This includes fabricating news articles to damage company reputation, creating fake LinkedIn profiles for long-term relationship building, or manufacturing "evidence" during negotiations.
Why AI Threats Represent an Existential Shift
AI doesn't just improve existing attacks—it fundamentally transforms their nature:
Scale: Launch simultaneous campaigns against thousands of targets instantlyPersonalization: Each victim receives uniquely tailored contentAdaptability: Real-time learning and optimization from successful attemptsCost reduction: Enterprise-level attack capabilities now accessible to individual criminals
The result is a democratization of cybercrime where small-scale actors wield enterprise-level offensive capabilities.
Building AI-Era Defenses: A Strategic Framework
Traditional security approaches are insufficient against AI-powered threats. Organizations must adopt intelligent, adaptive defense strategies:
1. Credential Security as Foundation
Compromised credentials remain the most profitable attack vector. Implement continuous monitoring for leaked usernames and passwords across deep and dark web sources. Deploy passwordless authentication where possible and mandate multi-factor authentication universally.
2. AI-Powered Threat Detection
Deploy machine learning systems that detect behavioral anomalies, identify suspicious patterns, and predict attack vectors. These systems must operate in real-time and adapt to emerging threat patterns.
3. Human-Centric Security Training
Combine regular security awareness training with AI-driven phishing simulations that mirror current attack sophistication. Train employees to verify unusual requests through independent communication channels.
4. Rapid Response Capabilities
Minimize dwell time through automated incident response workflows. Establish clear escalation procedures and practice scenario-based tabletop exercises regularly.
5. Continuous Security Posture Management
Replace periodic security audits with ongoing vulnerability assessment and remediation programs. Prioritize fixes based on actual exploitability and business impact.
Selki: Intelligence-Driven Cybersecurity for the AI Age
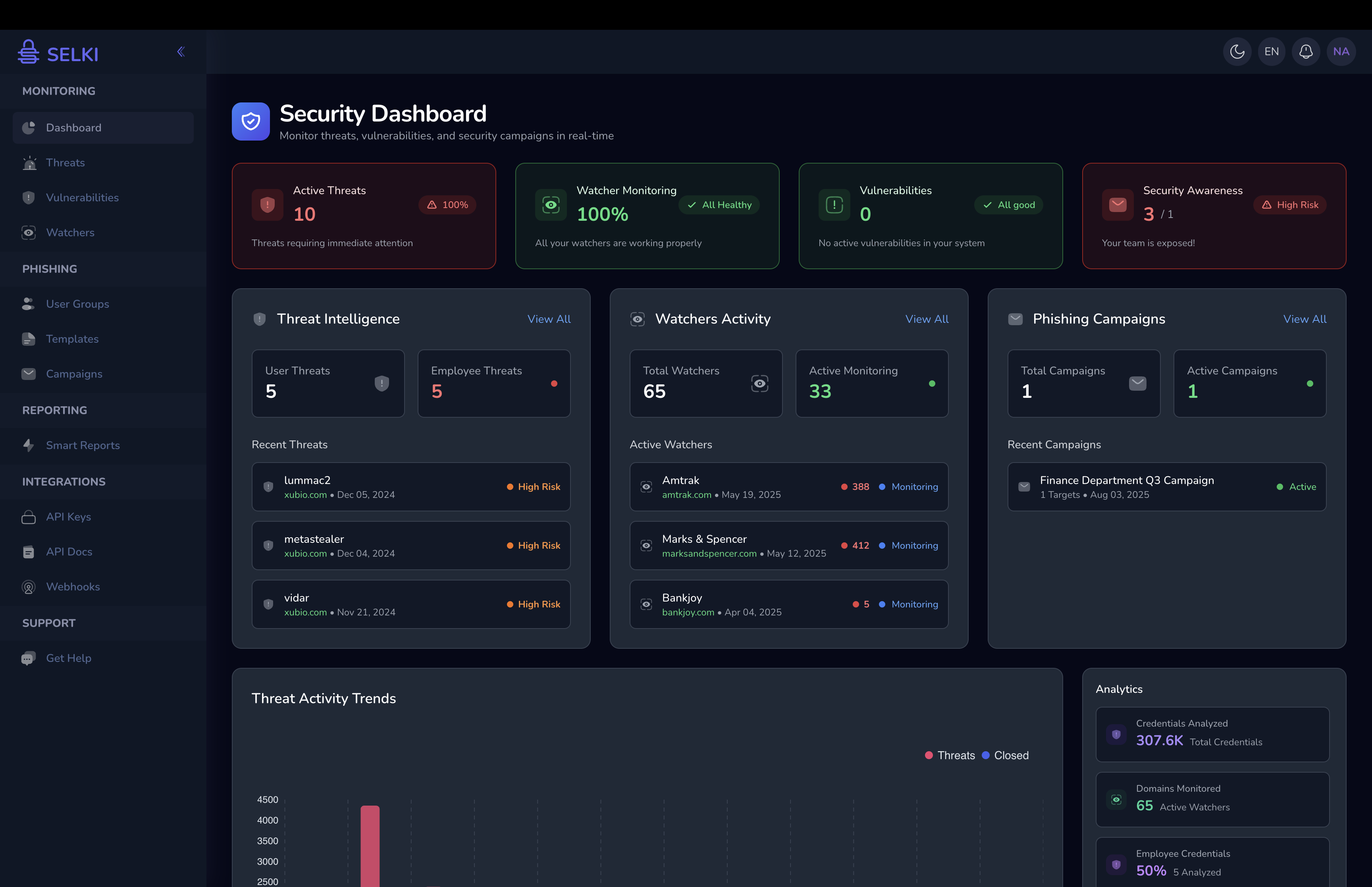
At Selki, we've built our platform specifically for the AI-driven threat landscape, combining advanced threat intelligence with actionable insights:
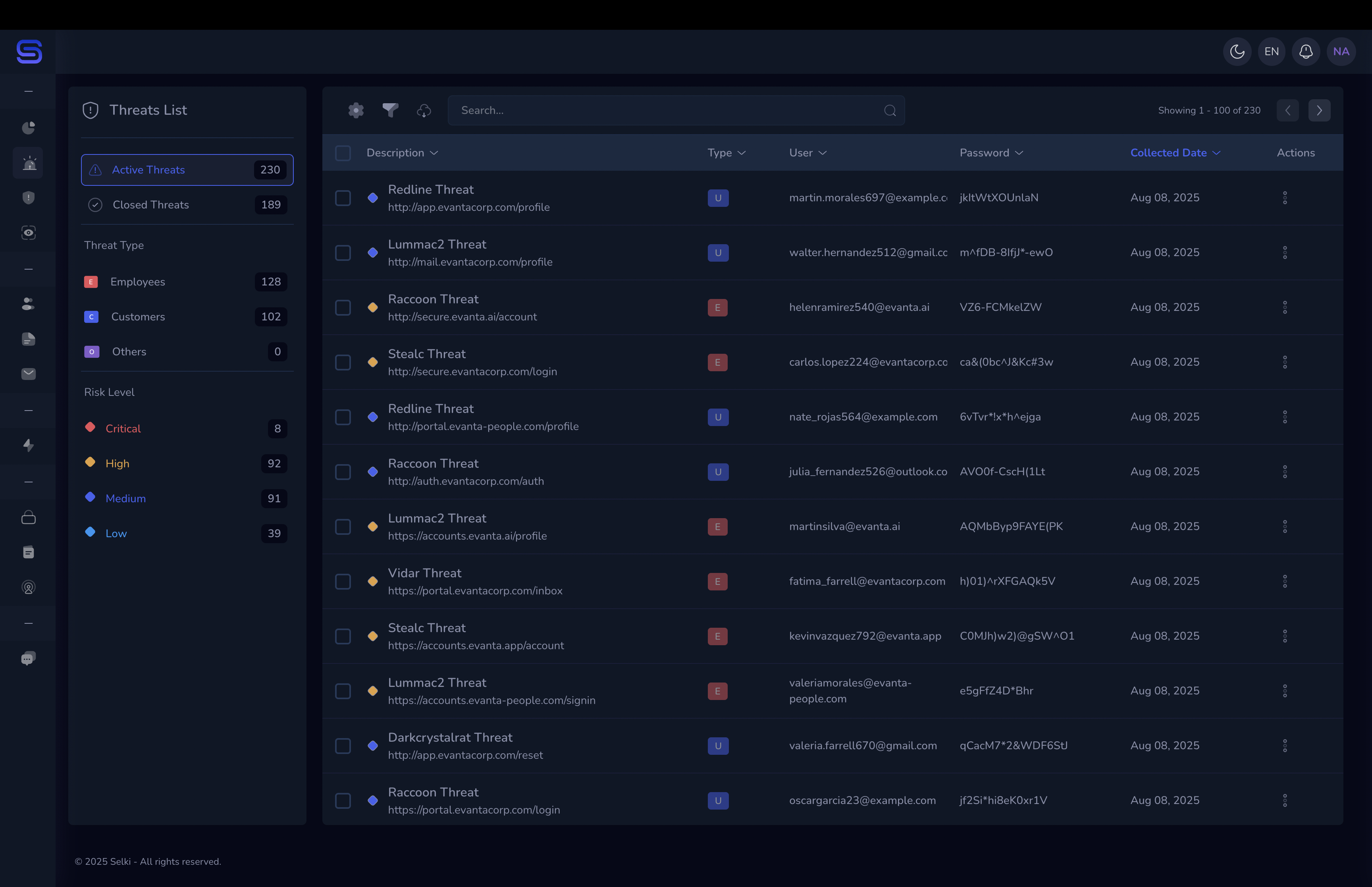
Comprehensive Credential Monitoring: Continuous surveillance across deep and dark web sources detects compromised credentials before attackers weaponize them.
Intelligent Risk Prioritization: Our AI-driven analysis translates complex threat data into clear, prioritized actions based on actual business risk and ROI.
Proactive Vulnerability Management: Identify and remediate system weaknesses before automated scanners find them.
Real-Time Threat Intelligence: Stay ahead of emerging threats with timely, contextual alerts that enable proactive defense rather than reactive response.
In an era where cybercriminals leverage automation and AI, manual, reactive security approaches guarantee failure. Selki provides the visibility, intelligence, and speed necessary to maintain defensive superiority against AI-powered threats.
The Path Forward in the AI Age
AI-powered cyberattacks represent the new baseline threat landscape. Organizations that thrive will be those that match AI-driven attacks with AI-enhanced defenses, combining human expertise with intelligent automation.
The question isn't whether your organization will face AI-powered threats—it's whether you'll be prepared when they arrive.
Ready to strengthen your defenses against AI-powered threats? Request a Selki demo and see how intelligence-driven cybersecurity can protect your organization.