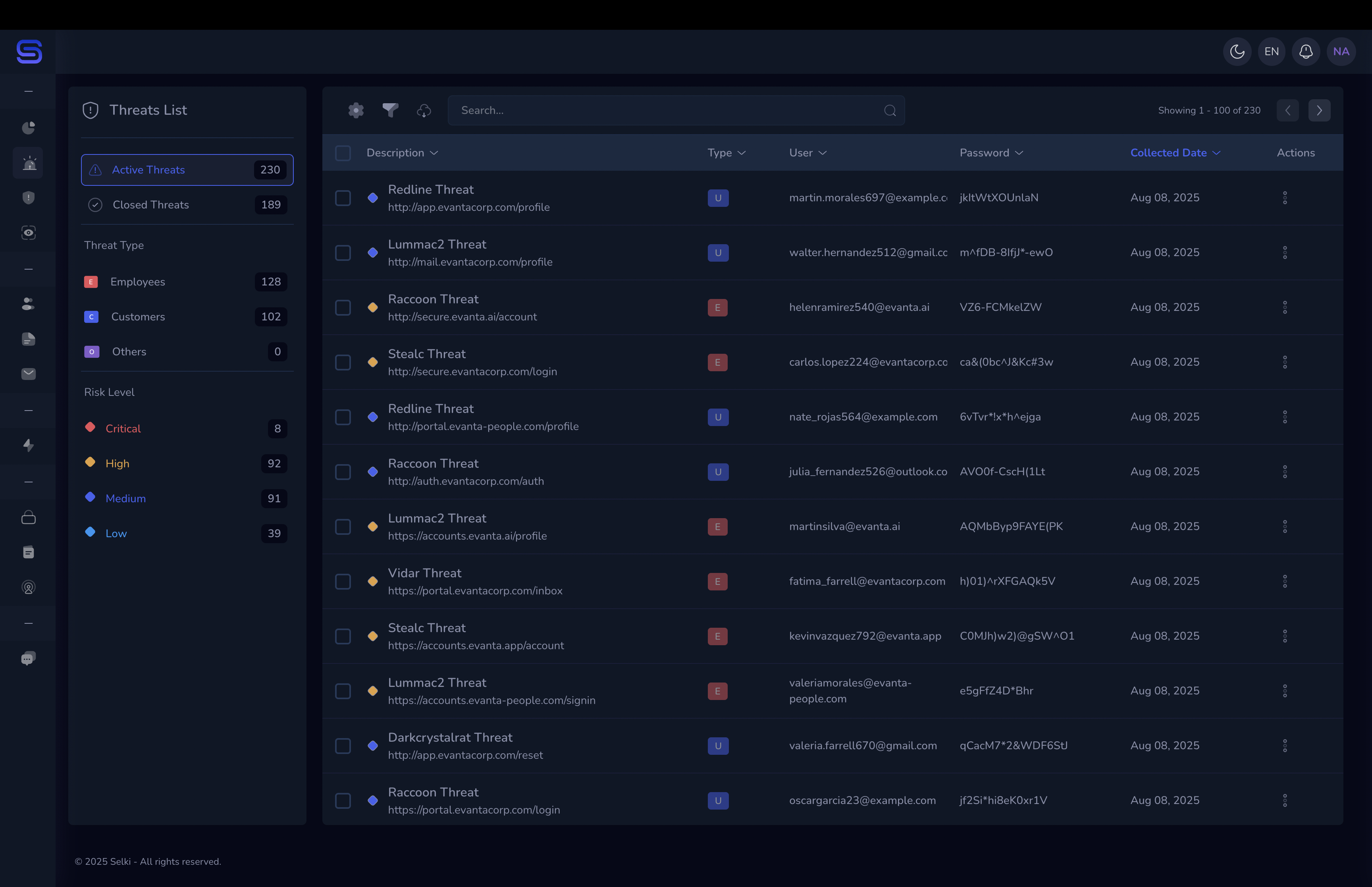
The dark web is a hidden part of the internet that isn't accessible through traditional browsers and search engines. It allows cybercriminals to anonymously trade stolen data, including usernames, passwords, and other sensitive information. For SMBs, compromised credentials often end up here, putting the entire business at risk of credential stuffing, account takeovers, and more.
When your business experiences a data breach, employee or customer credentials can be sold in “combo lists” — massive collections of usernames and passwords used by hackers to launch further attacks. Monitoring the dark web is essential to catching these compromised credentials early and taking action before they're exploited.
In this article, we'll discuss how hackers sell data on the dark web, how it impacts your business, and what you can do to protect your sensitive information.
How Hackers Exploit Stolen Data
Once hackers have stolen credentials, they often sell them on the dark web for profit. These credentials can be used in various types of attacks:
- Credential Stuffing. Hackers use stolen credentials to attempt logins on other systems, hoping users have reused the same password.
- Account Takeovers. With valid credentials, hackers gain access to sensitive accounts and can steal data or perform fraudulent transactions.
- Business Email Compromise (BEC). Compromised email accounts are often used in financial fraud, particularly in wire transfer scams.
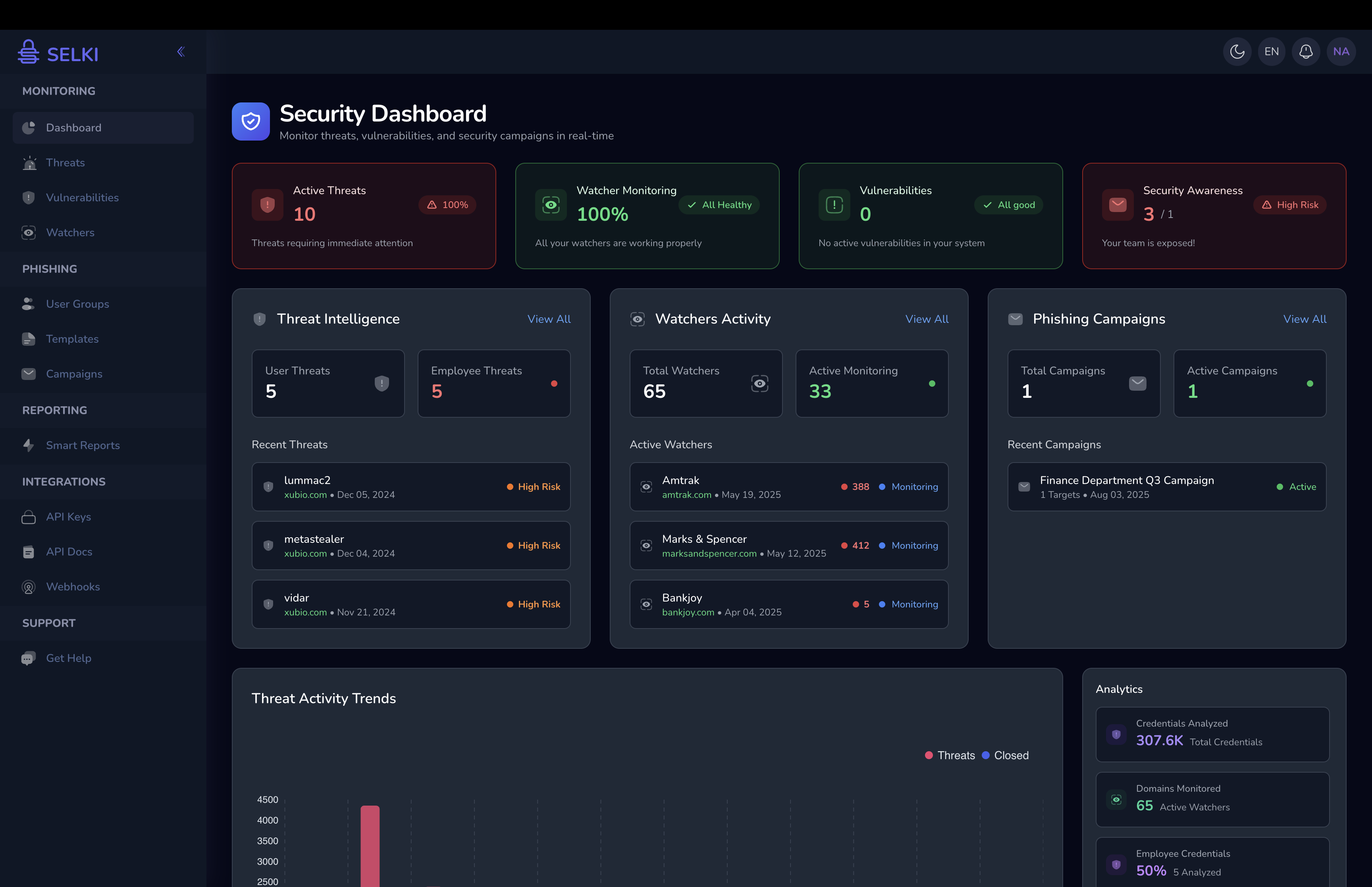
Why Dark Web Monitoring Matters for SMBs
Many SMBs are unaware that their credentials are being traded on the dark web. Hackers know that smaller businesses often lack the resources to detect or respond to these threats in time. This makes SMBs easy targets for credential stuffing and other forms of cyberattacks.
By using dark web monitoring tools like Selki, SMBs can continuously scan the dark web for compromised credentials associated with their business. Early detection allows companies to reset passwords and take security measures before these credentials are used in attacks.
"Thanks to Selki, we discovered compromised credentials before any damage was done. Their monitoring has been crucial in keeping our business secure."
― Juan Martinez - Owner, Martínez & Co.
How Can SMBs Protect Themselves?
To protect your business from credential compromise and dark web activity, consider these steps:
- Enable Multi-Factor Authentication (MFA). Adding MFA helps protect accounts, even if passwords are compromised.
- Use Strong, Unique Passwords. Encourage employees to use strong passwords and avoid reusing them across different systems.
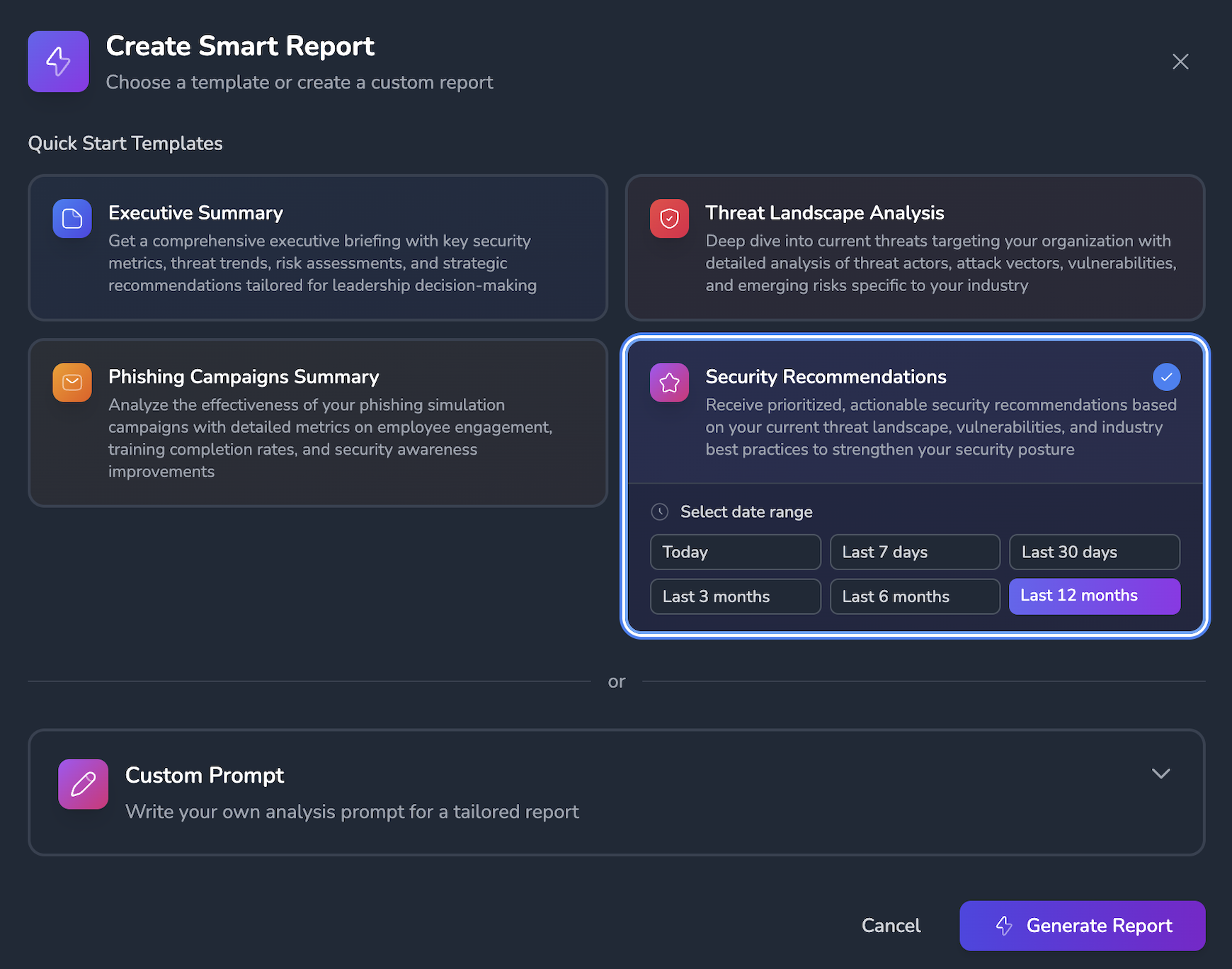
- Invest in Dark Web Monitoring. A service like Selki monitors the dark web in real-time for any compromised credentials related to your business.
- Train Employees on Cybersecurity. Regularly educate your team on the importance of recognizing phishing attempts and other cyber threats.
Key Takeaways and Recommendations
The dark web is where stolen credentials are often sold and used for cyberattacks like credential stuffing and account takeovers. SMBs are frequent targets due to weaker security measures. By enabling MFA, using strong passwords, and investing in dark web monitoring, businesses can protect themselves from these growing threats.
To keep your business safe, start by enabling MFA, educating your employees, and considering a service like Selki for continuous dark web monitoring.