Latin America is facing an alarming cyber threat in 2025: credential theft has skyrocketed by 160% globally, and several Latin American nations are among the hardest hit.
New research shows that Brazil and Argentina both rank in the top ten countries worldwide for compromised credentials—placing the region squarely in the crosshairs of cybercriminals.
This surge isn’t just a statistic — it’s a wake-up call. From financial institutions in São Paulo to tech startups in Buenos Aires, stolen credentials are opening the door to fraud, ransomware, and corporate espionage.
And with infostealer malware being sold as a cheap subscription service on the dark web, the barrier to entry for attackers has never been lower.
Top 10 Countries Most Affected by Credential Theft
Recent findings show that countries with the largest populations dominate the list, but others like Vietnam, Pakistan, and Turkey are emerging as unexpected hotspots — underscoring their expanding digital footprint and growing vulnerabilities.
| Rank |
Country |
| 1 |
United States |
| 2 |
India |
| 3 |
Brazil |
| 4 |
Mexico |
| 5 |
Argentina |
| 6 |
Vietnam |
| 7 |
Pakistan |
| 8 |
Turkey |
| 9 |
Indonesia |
| 10 |
Nigeria |
While the full ranked list isn’t published in exact order, Brazil and Argentina are specifically highlighted among the top ten.
The Unsettling Rise of Credential Theft in 2025
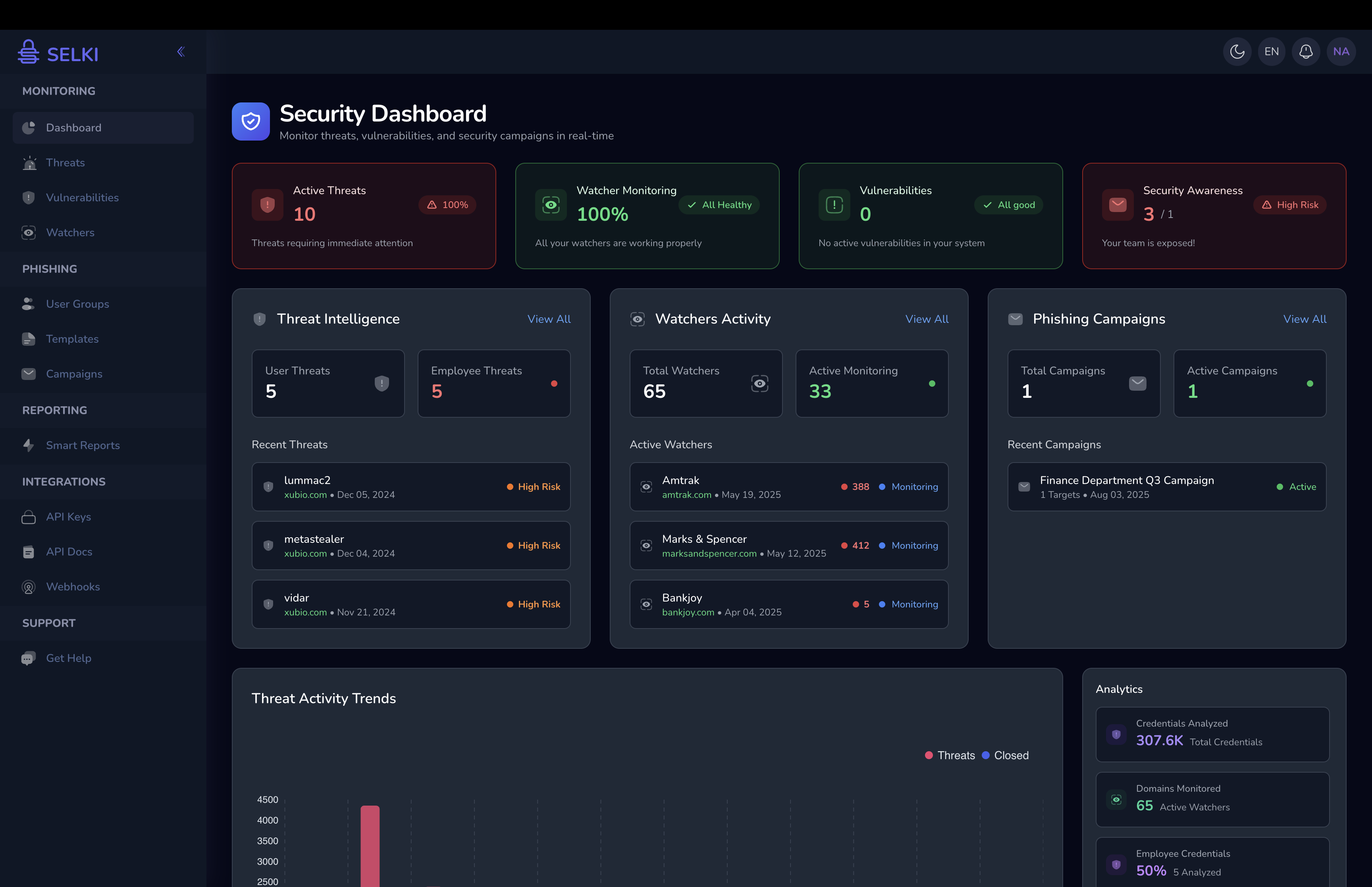
Recent findings reveal a shocking 160% surge in credential theft so far in 2025 compared to 2024. In just one month, organizations reported over 14,000 cases where employee credentials were exposed — even within systems adhering to established password policies.
Credential theft is fast becoming one of the most common causes of security breaches. In fact, leaked credentials accounted for 22% of breaches in 2024, surpassed only by phishing and software exploits.
Why Are Credential Theft Attacks Spiking?
Three key factors are fueling this alarming rise:
- Infostealer malware delivered via Malware-as-a-Service (MaaS): This enables even low-skilled attackers to launch credential theft campaigns with ease.
- AI-enhanced phishing: AI-generated phishing emails now mimic tone, imagery, and branding with alarming realism, making them far more convincing than ever.
- Slow response times: When credentials leak — especially through developer platforms like GitHub — businesses take an average of 94 days to revoke access or disable compromised accounts.
The Real-World Fallout
Once stolen, credentials become a “universal skeleton key” for attackers: cheap to purchase, easy to weaponize, and often valid for months. These stolen credentials circulate across underground markets, Telegram channels, and hacking forums — extending the window of risk for organizations.
How Companies and Users Can Defend Themselves?
- Enable Multi-Factor Authentication (MFA): MFA significantly bolsters security — one study found it reduces the risk of compromise by over 99%, with MFA‑enabled accounts remaining secure in over 99.99% of cases.
- Use Unique, Strong Passwords and Password Managers: Avoid password reuse across sites. Employ password managers to generate and store complex, unique credentials, making credential stuffing attacks far less effective.
- Implement Compromised-Credential Checking Services like browser-based password checkers—leveraging secure hashing and k-anonymity models—can alert users when their credentials have been exposed, without compromising privacy.
- Monitor & Respond Faster Treat credential exposure as a live, operational risk—not something to audit quarterly. Rapid detection and revocation of compromised credentials are critical.
- Fortify Against Infostealers Train employees to recognize phishing, avoid suspicious downloads (including pirated software or unknown browser extensions), and deploy endpoint protection to detect infostealer activity.
You Need a Real-Time Credential Defense Partner
As this rising tide of credential theft makes clear, static policies and delayed responses are no longer enough. That’s where Selki steps in as the perfect tool for modern security teams.
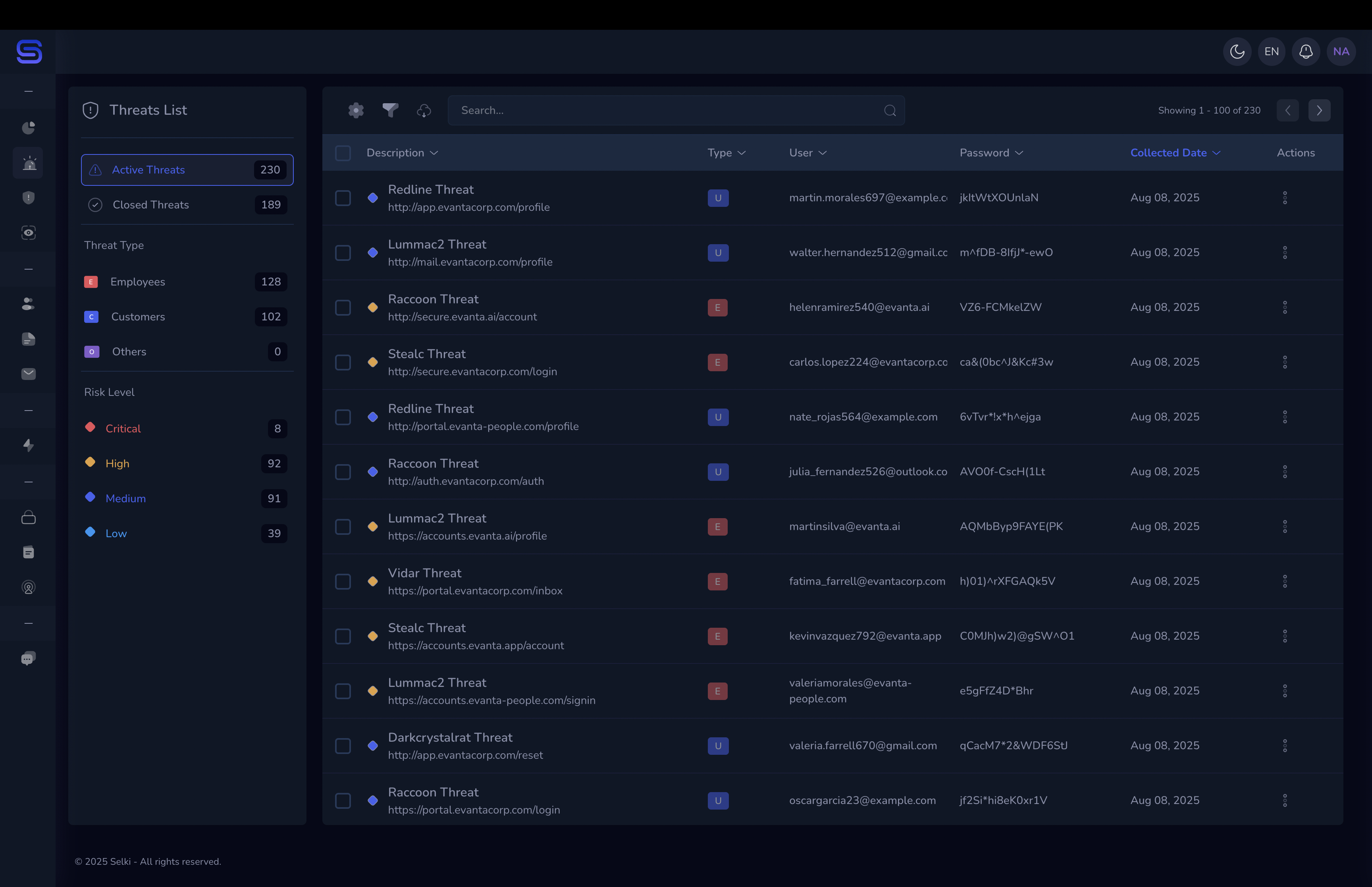
Selki provides companies with real-time alerts and deep insights into credential compromises—direct from infostealer logs. This means you:
- Accelerate response times: revoke access, rotate credentials, and remediate risks before widespread damage occurs.
- Detects exposed credentials the moment they appear, not weeks later.
- Gain visibility into which accounts or employees are affected.
With Selki, you transform sluggish remediation into agile, proactive defense—exactly the kind of solution required in the age of credential-based threats.
Final Thoughts
The 160% spike in credential theft in 2025 isn't a distant statistic — it’s a clear warning. But with strategies like rapidly detecting leaks, enforcing MFA, promoting strong password hygiene, and leveraging advanced platforms like Selki, companies can fight back effectively.
Stay alert, act swiftly, and make sure every credential remains under your control — not theirs!