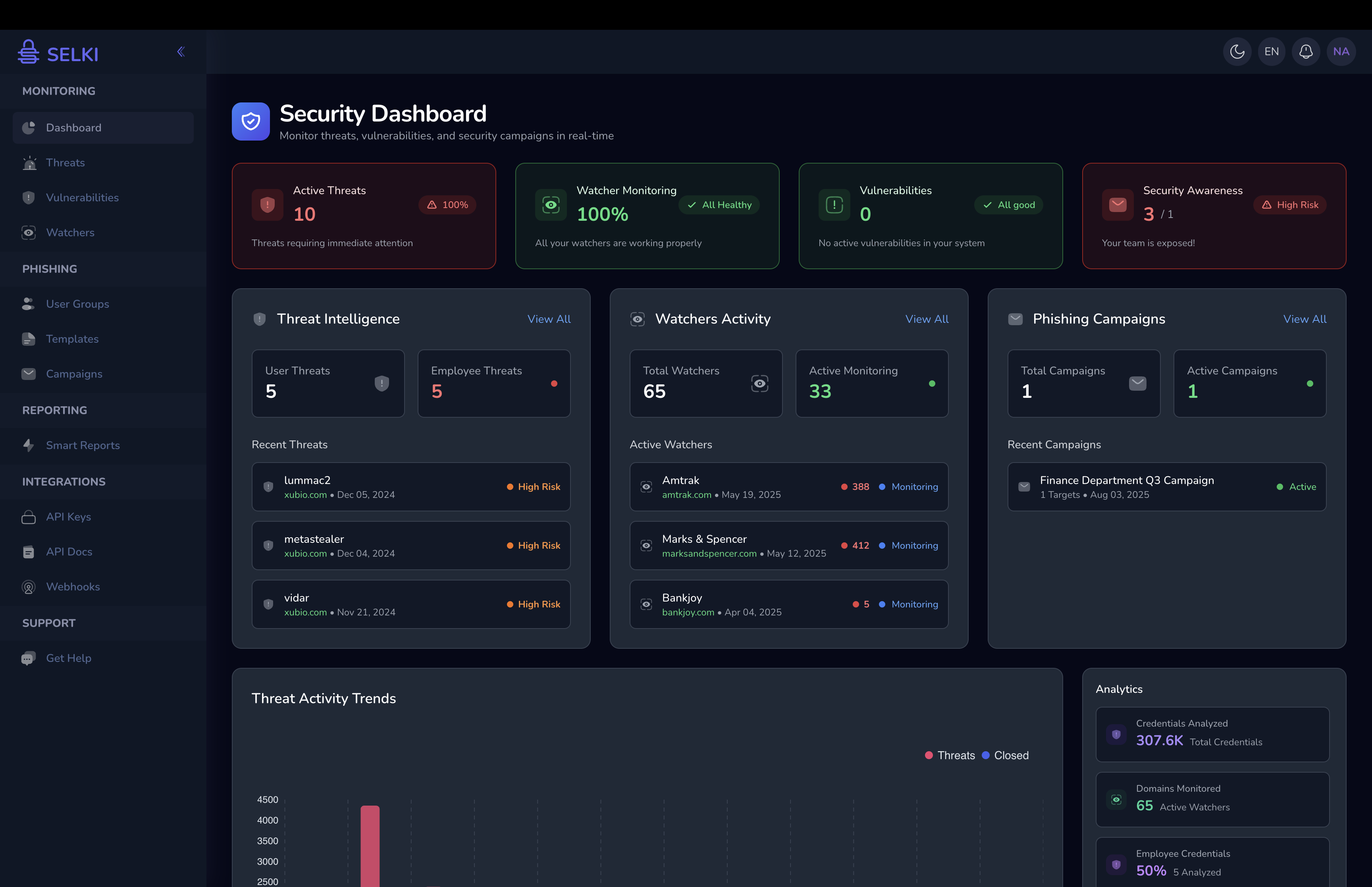
In today's digital world, no business is too small to be targeted by cybercriminals. Small and medium-sized businesses (SMBs) are increasingly falling victim to credential theft—where login details, usernames, and passwords are stolen and used for malicious purposes. SMBs often have fewer security measures in place compared to larger enterprises, making them easier targets for cyberattacks.
Credential compromise is a gateway for hackers to gain unauthorized access to business systems, sensitive customer data, and financial information. Once these credentials are stolen, they can be sold or exchanged on the dark web, allowing bad actors to carry out further attacks, such as identity theft, phishing, or financial fraud.
Understanding credential compromise is critical for any SMB looking to protect its digital assets. In this article, we'll explore what credential compromise is, how it works, and — most importantly — how you can protect your business.
What is Credential Compromise?
Credential compromise refers to the unauthorized acquisition of login credentials—typically usernames and passwords — by malicious actors. These credentials are often obtained through:
- Phishing attacks. Tricking employees or individuals into revealing their login information via deceptive emails or websites.
- Data breaches. Hackers breach a company's system and steal login details from databases.
- Password reuse. Many employees reuse the same password across different accounts. If a hacker gets hold of a password from a less secure platform, they can attempt to use it elsewhere.
- Malware. Infostealer malware can extract passwords directly from devices, often without the victim's knowledge.
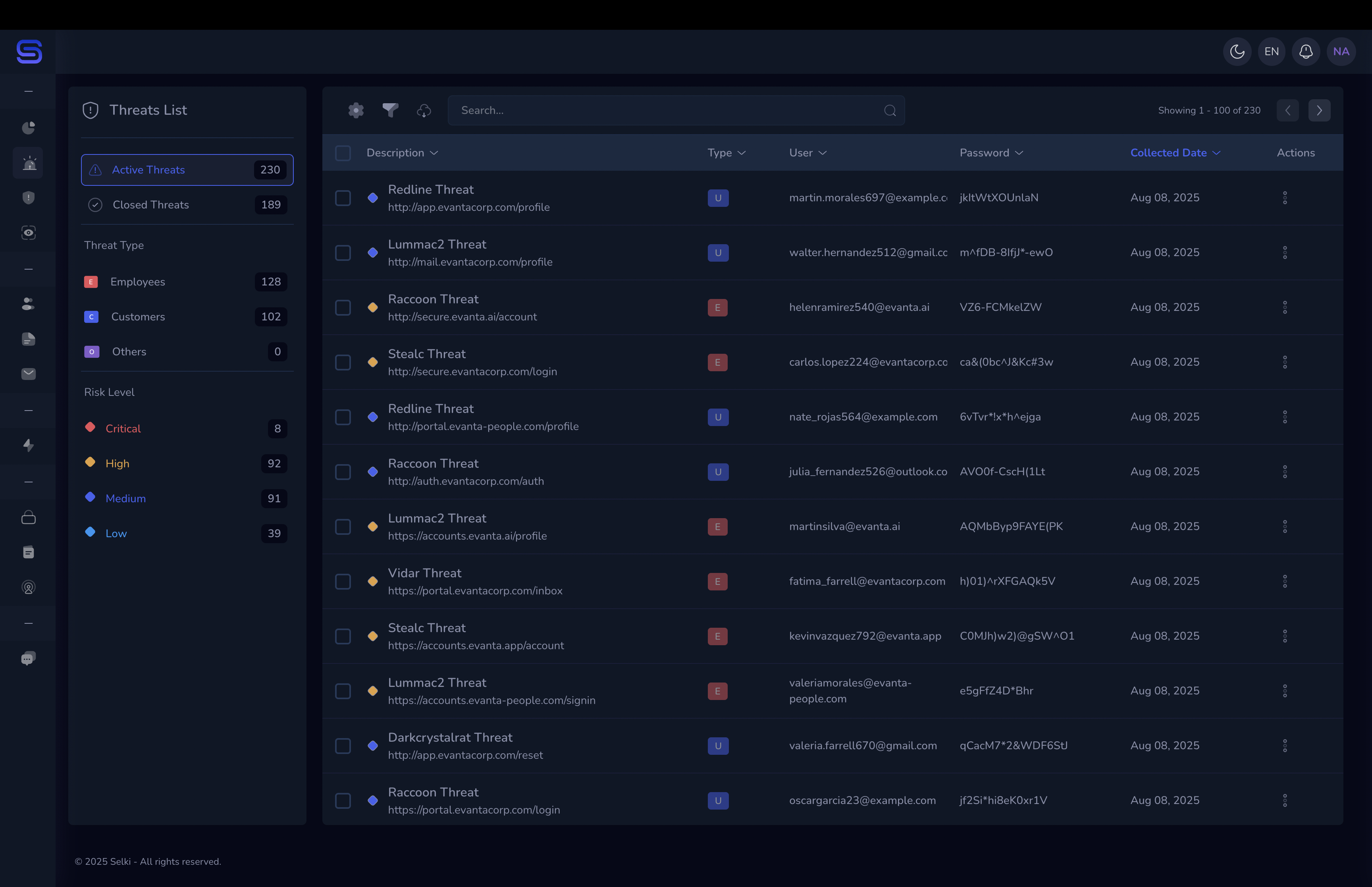
Once stolen, these credentials can be sold on the deep and dark web in whatss known as “combo lists” — massive databases of usernames and passwords that hackers use for future attacks, such as credential stuffing or account takeovers.
Why Are SMBs a Prime Target?
Many SMBs believe they are not lucrative enough to be targeted by hackers. However, the opposite is true. In fact, 65% of cyberattacks now target SMBs. There are a few reasons why:
- Weaker Security. Many SMBs lack the resources to implement advanced security measures like multi-factor authentication (MFA) or intrusion detection systems.
- Outdated software. Smaller businesses may not regularly update their software and systems, leaving vulnerabilities open for exploitation.
- Lower cyber awareness. Employees at SMBs may not be trained in recognizing phishing emails, social engineering, or other cyber threats.
- Password reuse. It's common for employees at smaller businesses to use the same password across multiple systems, which increases the risk of compromise if one account is breached.
So, what is the result? SMBs often find themselves on the losing end of a credential compromise, potentially facing regulatory fines, loss of customer trust, and operational disruption.
"Thanks to Selki, we discovered compromised credentials before any damage was done. Their monitoring has been crucial in keeping our business secure."
― Maria Hill - Security Manager
How Do Hackers Use Stolen Credentials?
Once cybercriminals have compromised your business's credentials, the possibilities for further attacks are endless. These include but are not limited to:
- Credential stuffing. Using automated tools, hackers attempt to log into a variety of systems and accounts using the stolen credentials, hoping that users have reused the same password elsewhere.
- Account takeover. With valid login details, hackers can take over user accounts, steal data, and engage in fraudulent activities.
- Business email compromise (BEC). Hackers may use stolen credentials to gain access to email accounts, leading to wire fraud or other financial scams.
- Ransomware deployment. With administrative-level access, hackers can lock SMBs out of their systems and demand payment to regain control.
The impacts of these attacks can be devastating to an SMB, leading to financial losses, legal consequences, and reputational damage often in range of hundreds of thousands of dollars. More than 80% of cyber security incidents worldwide are initiated through credential breach.
How Can SMBs Protect Themselves?
Now that you understand the risks, let's discuss the steps your SMB can take to protect itself from credential compromise. Here are some of the most effective measures:
- Enable multi-factor authentication (MFA). This is one of the simplest and most effective ways to protect your business. MFA adds an extra layer of security by requiring users to provide an additional verification factor (such as a code sent to their phone) before accessing accounts.
- Use strong, unique passwords. Employees should be encouraged (if not required) to use strong, unique passwords for each account. A password manager can help generate and store these passwords securely.
- Regularly monitor for credential compromise. Monitoring tools, like Selki, scan the deep and dark web for any instances of your company's credentials being sold or traded. Early detection can help prevent further attacks before they occur.
- Train and test your employees. Employees should be trained to recognize phishing attempts and other forms of social engineering. Regular security awareness training can significantly reduce the chances of credential compromise.
- Implement a “Zero Trust” policy. Zero Trust security assumes that no one—inside or outside your network—can be trusted by default. Access to systems and data should be granted on a need-to-know basis, and all access should be regularly reviewed.
- Update and patch regularly. Ensure that all software and systems are kept up-to-date to minimize the chances of vulnerabilities being exploited.
Credential compromise is a growing threat that no business can afford to ignore. By taking proactive steps, SMBs can stay ahead of hackers and keep their systems and customer data secure.
Key Takeaways and Recommendations
Credential compromise poses a significant threat to SMBs, often resulting in severe financial and reputational harm. Cybercriminals target SMBs due to their typically weaker security measures compared to larger organizations. Once credentials are stolen, they are sold or traded on the dark web, giving hackers access to critical business systems. However, SMBs can protect themselves by implementing multi-factor authentication (MFA), enforcing strong password policies, monitoring for compromised credentials, training employees on cybersecurity, and ensuring their systems are regularly updated.
To strengthen your business's defenses, begin using MFA immediately if it's not already in place. This simple step can greatly enhance your security. Additionally, investing in dark web monitoring services, such as those offered by Selki, can help detect compromised credentials before they're exploited. Finally, make cybersecurity training a regular part of your team's routine to help employees recognize potential threats, such as phishing attacks, and minimize risks.