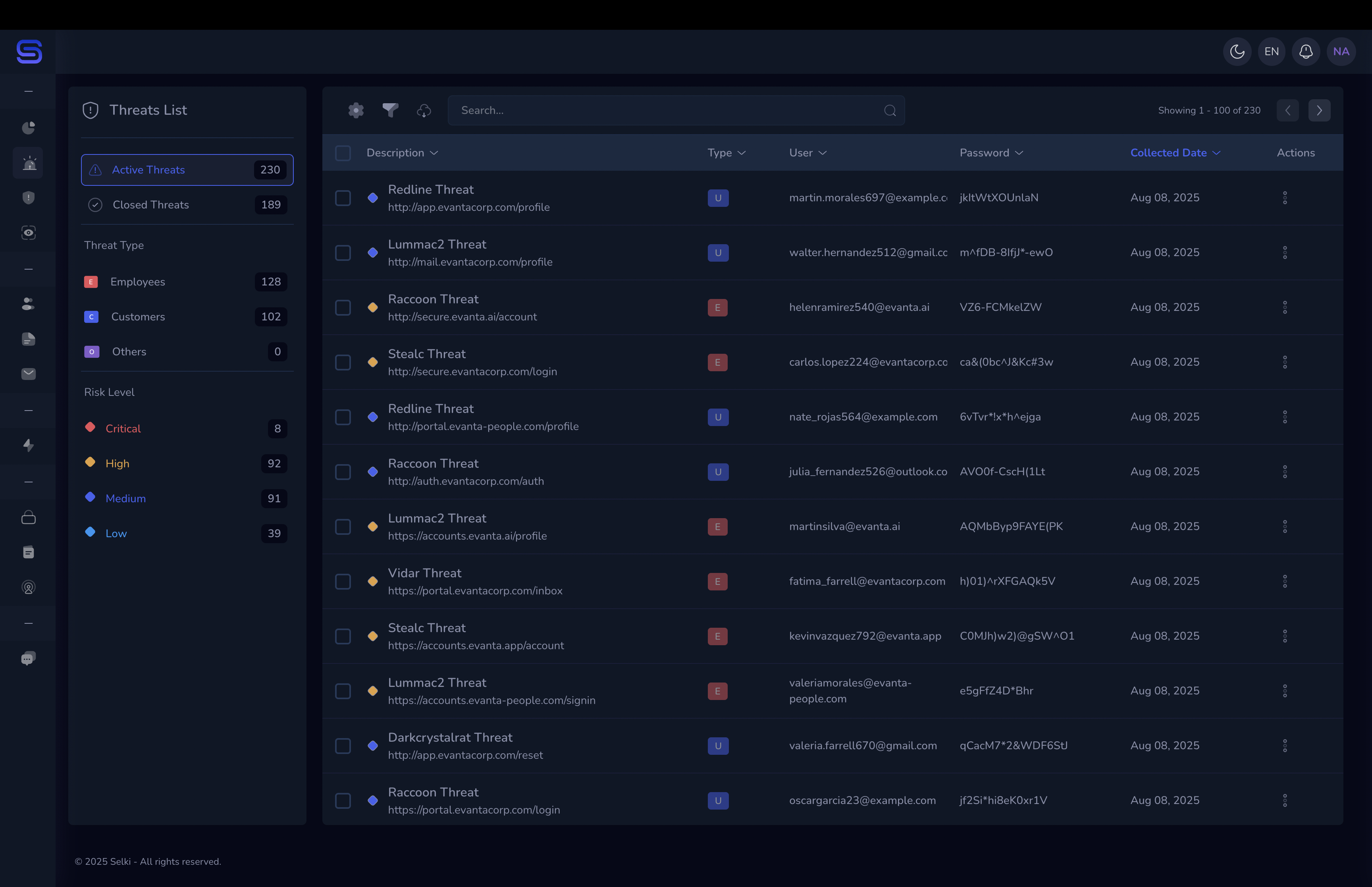
Infostealer malware is a type of malicious software designed to extract sensitive information, such as usernames, passwords, browser data, and even financial information, directly from your employees' devices. This malware often operates silently in the background, making it difficult to detect until it's too late.
Once hackers have collected this information, they can sell it on the dark web or use it to gain access to your business systems, compromising both your data and that of your clients. Given the growing sophistication of infostealer malware, protecting your business from this type of cyberattack has become more critical than ever.
In this article, we'll explain how infostealer malware works, how it affects businesses, and the steps you can take to secure your business against this growing threat.
How Does Infostealer Malware Work?
Infostealer malware is typically delivered through phishing emails, malicious attachments, or infected websites. Once installed, the malware begins collecting sensitive data from the victim's device. This data can include
- Login Credentials. The malware captures usernames and passwords for both personal and business accounts.
- Browser Data. Hackers can steal cookies and session data, giving them access to online accounts.
- Financial Information. Infostealers can capture credit card details and banking information stored on a device.
Once collected, the data is either used directly for credential theft or sold on the dark web in combo lists, where it can be accessed by other cybercriminals.
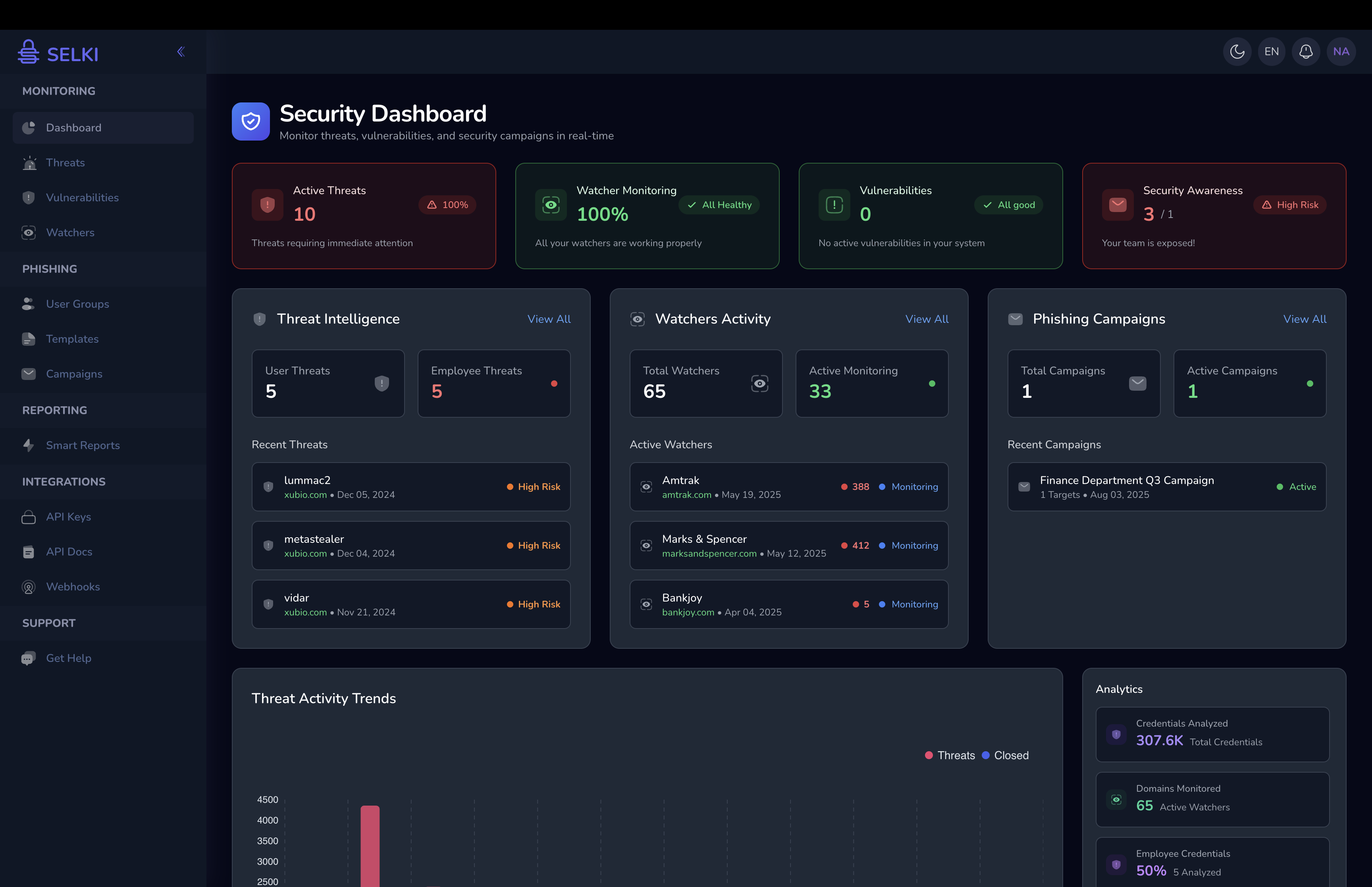
The Impact of Infostealer Malware on SMBs
SMBs are at significant risk from infostealer malware due to their typically limited cybersecurity resources. Once hackers gain access to stolen credentials or financial data, they can compromise your systems, steal sensitive information, and cause major disruptions to your operations.
Infostealer attacks can result in significant financial losses, as well as damage to your reputation. Clients and partners may lose trust in your ability to safeguard their data, leading to lost business and legal ramifications.
"We were unaware that infostealer malware had compromised our systems until Selki detected it. Thanks to their dark web monitoring, we were able to stop the malware before it caused further damage."
― Carlos Rivera- CEO, Rivera Consulting
How Can SMBs Protect Themselves from Infostealer Malware?
Protecting your business from infostealer malware requires a combination of strong security practices and proactive monitoring. Here are some steps you can take:
- Use Advanced Anti-Malware Solutions. Ensure that all devices on your network have up-to-date anti-malware protection to prevent infections.
- Enable Multi-Factor Authentication (MFA). Even if credentials are stolen, MFA can help prevent unauthorized access to accounts.
- Invest in Dark Web Monitoring. Services like Selki can detect when your company's credentials are sold on the dark web, allowing you to respond quickly.
- Regularly Train Employees. Educate your team on the risks of phishing and how to avoid clicking on suspicious links or downloading untrusted attachments.
Key Takeaways and Recommendations
Infostealer malware can silently extract sensitive data from your business, including login credentials and financial information. SMBs are especially vulnerable to these attacks, which can lead to significant financial losses and reputational damage. By implementing strong anti-malware solutions, enabling MFA, and investing in dark web monitoring, businesses can significantly reduce the risk of infostealer malware attacks.
Take steps today to protect your business by using anti-malware tools, educating your employees, and considering Selki's dark web monitoring service to detect compromised credentials before they are exploited.